Generate and manage SBOM
A Software Bill of Materials (SBOM) is essential for understanding the components and dependencies within an application, which in turn enables organizations to manage open-source component risks effectively.
The Harness SSCA module provides comprehensive capabilities for generating, managing, and analyzing SBOM for software artifacts.
Integration with other Harness modules and third-party tools
The SSCA module integrates with the CI and CD stages of Harness pipelines, ensuring that an SBOM is generated for every build of your software artifacts and, optionally, before deployment, as well. This helps you maintain up-to-date information about the components used in your applications at all times. Additionally, you have the flexibility to use your preferred SBOM generation tool.
The SSCA module can also integrate with third-party SBOM generation tools, such as Syft. In the SSCA module, this is referred to as orchestrating with a tool, and it allows you to use your preferred SBOM generation tools or tools standardized and approved by security and governance teams.
SBOM formats
SSCA can generate SBOM in popular standard formats, such as CycloneDX and SPDX.
Because there are multiple SBOM formats and standards, the SSCA module normalizes your SBOM to extract the relevant information, such as component name, version, supplier, and licensing data. This normalization process ensures that your SBOM data is consistent, easy to manage, and can be used for policy enforcement and further analysis.
Attest and store
When an SBOM is generated, the SSCA module generates and signs the attestation, ensuring that the information is accurate and trustworthy. The attestations are then securely stored in your artifact repository, where you can access and analyze them as needed. SBOM are also stored in the Harness Platform so that you can download, analyze, and share them as needed.
Attestations are stored as .att files in the artifact repository, specified in your build or deploy stage, along with the image. You can also find the SBOM on the Execution details page in Harness. For more information, go to view pipeline execution results.
While Harness is capable of generating SBOMs for both Container Images and Code Repositories, it is important to note that SBOM attestation is supported only for Container Images.
Generate SBOM in Harness
These instructions describe how to generate SBOM with the Harness SSCA Orchestration step. This step uses Syft. For other SBOM tools, go to Ingest SBOM. For information about enforcing SSCA policies, go to Enforce SSCA policies
Prepare a pipeline
To generate SBOM in Harness, you need a pipeline with a CI (build) stage, a CD (deploy) stage, or both.
SBOM generation and enforcement architecture
These example demonstrate how you could set up Build and Deploy stages to generate SBOM and enforce policies.
- Build stage
- Deploy stage
This example Build stage has three steps:
- Run step: Build and test an artifact (image).
- Build and Push an image to Docker Registry step: Build and push the image to a Docker registry.
- SSCA Orchestration step: Generate the SBOM.
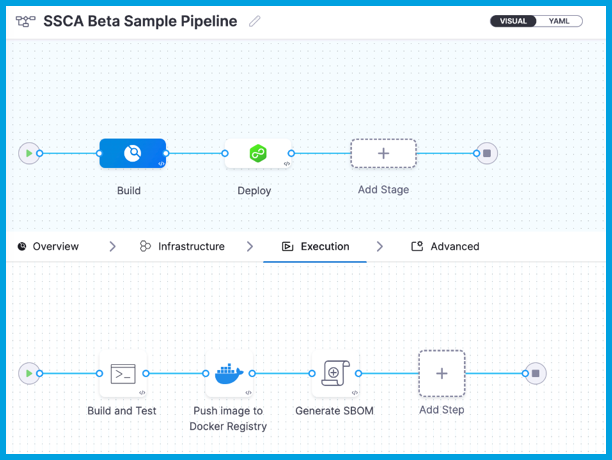
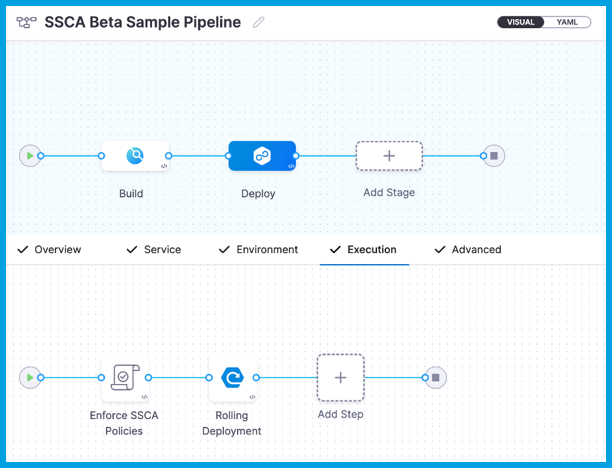
This example Deploy stage has two steps:
- SSCA Enforcement step: Enforce SSCA policies.
- Rolling deployment step: Based on the results of the policy evaluation, deploy the image.
Generate a key pair
Keys are used to sign and verify attestations.
- Use Cosign to generate a public and private key pair
- Create two Harness file secrets, one for the private key file and one for the public key file.
- Create a Harness text secret to store the password for the private key.
Add the SSCA Orchestration step
Use the SSCA Orchestration step to generate an SBOM in either the Build or Deploy stage of a Harness pipeline.
- In a Build stage, add the SSCA Orchestration step after the artifact (image) has been pushed to an artifact repository.
- In a Deploy stage, add the SSCA Orchestration step before the deployment step.
SSCA Orchestration and Enforcement steps in deploy stage can only be used in the Containerized Step Groups
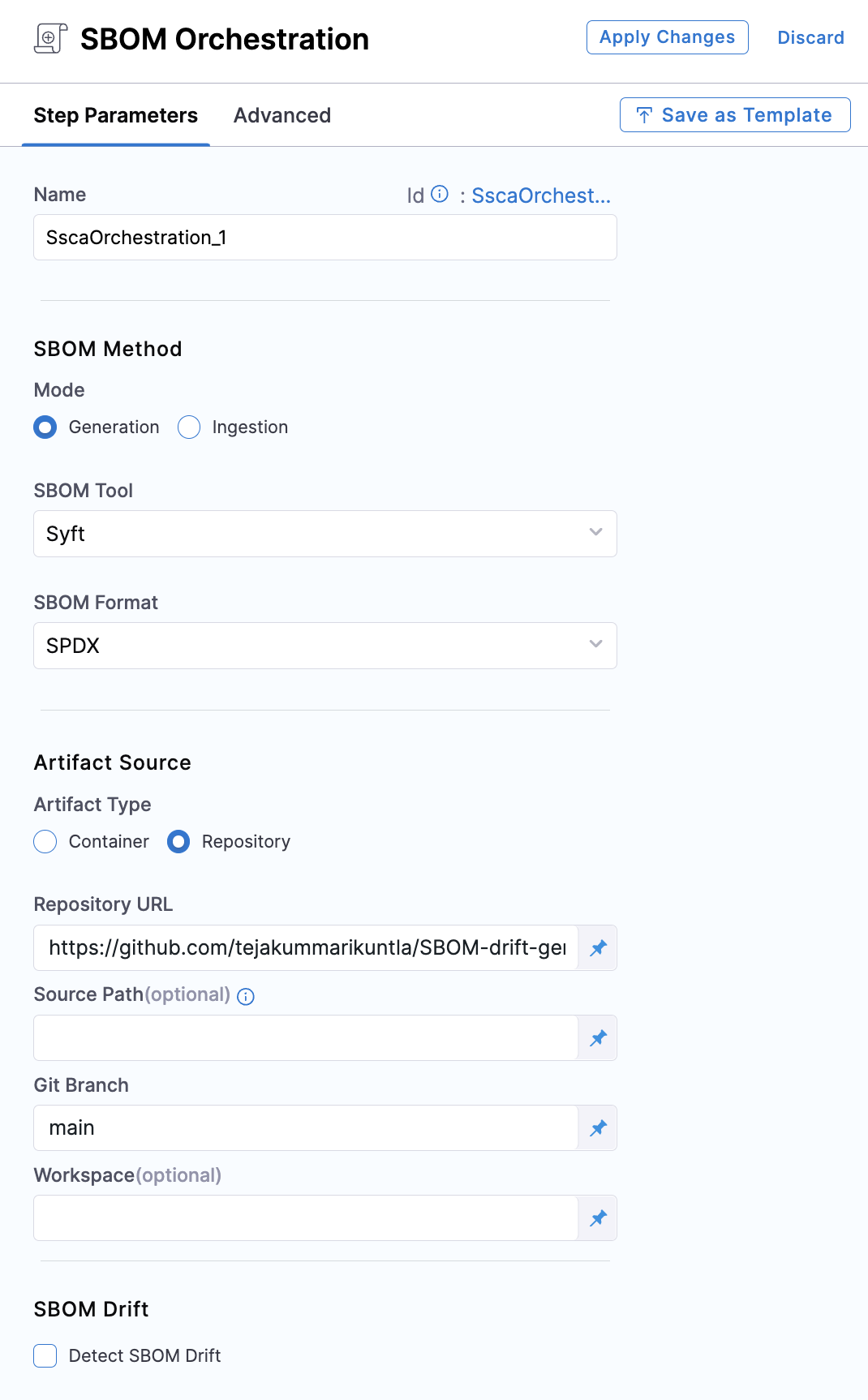
The SSCA Orchestration step includes various settings for generating the SBOM for both Containers and Repositories. We will delve into the different fields that need to be configured for each option to support the generation of the SBOM.
-
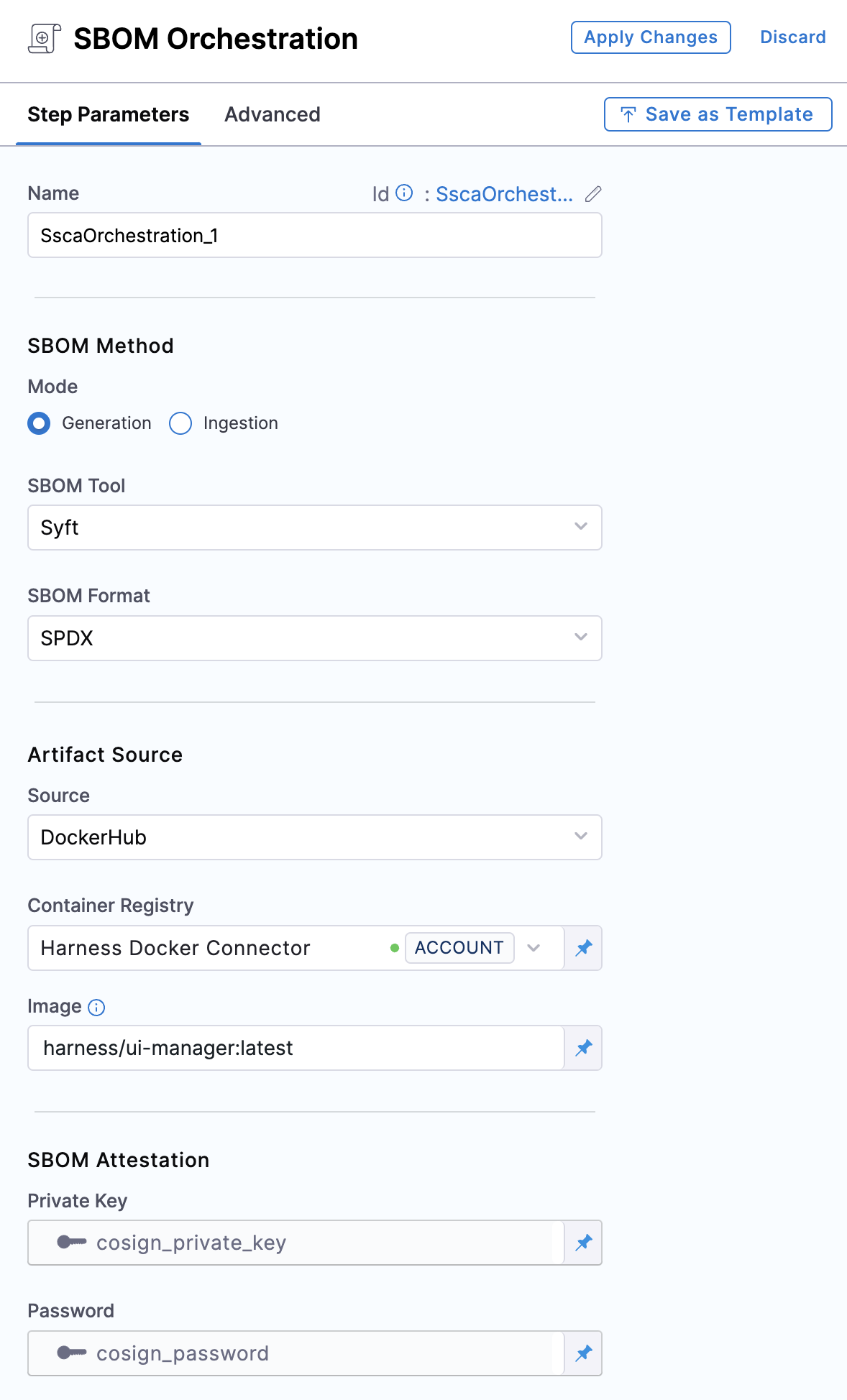
Name: Enter a name for the step.
-
Step Mode: Select Generation.
-
SBOM Tool: Select Syft, which is the tool Harness uses to generate the SBOM. For other SBOM tools, go to Ingest SBOM.
-
SBOM Format: Select SPDX or CycloneDX.
The Artifact Source allows you to specify the source of the artifact. Presently, the SBOM Orchestration step supports both containers and code repositories. Specifically for containers, it offers native support with DockerHub and ECR. Here's how you can configure them accordingly.
Please note that the previously available Container option, has now been deprecated. In its place, we now offer native support for DockerHub and ECR. Additionally, the support for other registries like GCR (Google Container Registry) and ACR (Azure Container Registry) is coming soon. We encourage users to connect to their registries using the dedicated options available within the list of artifact sources.
- DockerHub
- ECR
- Repository
-
Artifact Type: Select DockerHub.
-
Container Registry: Select the Docker Registry connector that is configured for the DockerHub container registry where the artifact is stored.
-
Image: The repo path (in your container registry) and tag for the image for which you're generating an SBOM, such as
my-docker-repo/my-artifact:latest. -
Private Key: The Harness file secret containing the private key to use to sign the attestation.
-
Password: The Harness text secret containing the password for the private key.
-
SBOM Drift: This feature allows you to track changes in SBOMs, it can detect the changes by comparing the generated SBOM against a specified one. For an in-depth understanding of this functionality, please refer to the SBOM Drift documentation. If you prefer not to detect any changes in SBOMs, leave this option unchecked.
If you're using Docker-compliant GCR or ACR repositories:
- You can use
DockerHubas the artifact source - Configure your Docker Registry connector as a valid artifact source.
- For GCR, go to Use Docker Registry for GCR
- For ACR, go to Use Docker Registry for ACR
- Use the full URI for the Image in your SSCA Orchestration step, such as
1234567890.dkr.ecr.REGION.amazonaws.com/IMAGE_NAME:TAG.
-
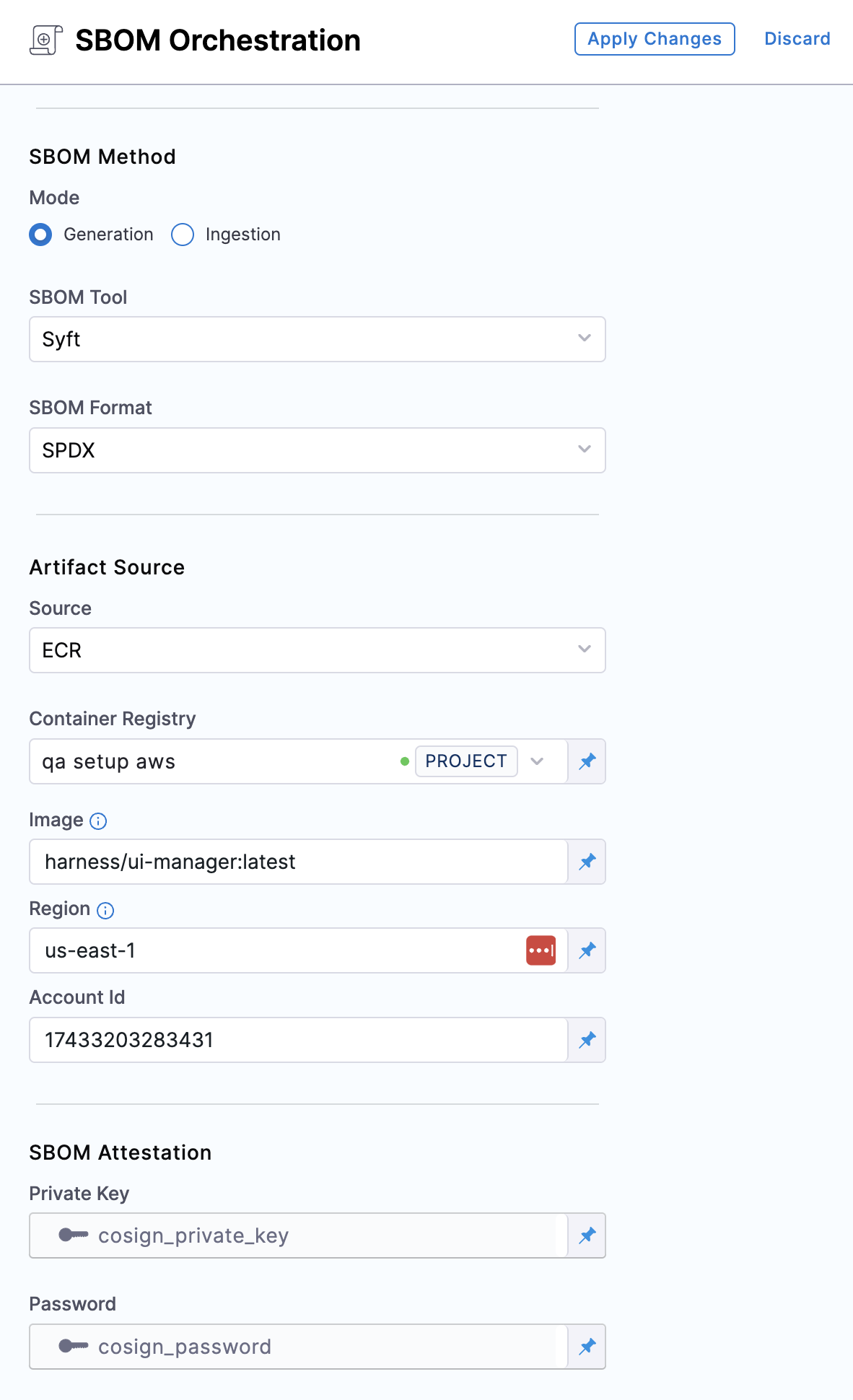
Artifact Type: Select ECR.
-
Container Registry: Select the Docker Registry connector that is configured for the Elastic container registry where the artifact is stored.
-
Image: The repo path (in your container registry) and tag for the image for which you're generating an SBOM, such as
my-docker-repo/my-artifact:latest. -
Region: The geographical location of your ECR repository.
-
Account ID: The unique identifier associated with your AWS account.
-
Private Key: The Harness file secret containing the private key to use to sign the attestation.
-
Password: The Harness text secret containing the password for the private key.
-
SBOM Drift: This feature allows you to track changes in SBOMs, it can detect the changes by comparing the generated SBOM against a specified one. For an in-depth understanding of this functionality, please refer to the SBOM Drift documentation. If you prefer not to detect any changes in SBOMs, leave this option unchecked.
If you're using Docker-compliant GCR or ACR repositories:
- You can use
DockerHubas the artifact source - Configure your Docker Registry connector as a valid artifact source.
- For GCR, go to Use Docker Registry for GCR
- For ACR, go to Use Docker Registry for ACR
- Use the full URI for the Image in your SSCA Orchestration step, such as
1234567890.dkr.ecr.REGION.amazonaws.com/IMAGE_NAME:TAG.
-
Artifact Type: Select Repository.
infoThe Repository option requires that your repository is cloned into the stage workspace before the SSCA Orchestration step runs. There are several ways you can do this:
- Clone the codebase by default, such as a Build stage's default codebase.
- Add a Git Clone step or Run step to the Deploy stage.
- Add a Git Clone step or Run step to a Build stage.
-
Repository URL: The Repository URL you've configured for cloning into the workspace.
-
Source Path: Leave blank or enter a path (in the repository) for which you want to generate SBOM. Use this setting to generate SBOM for a specific section of your code repo, rather than your entire repo. The path must start with
/. For example, if your repository URL ishttps://github.com/username/repo, and you want to generate SBOM forhttps://github.com/username/repo/service-core/source, then enter/service-core/sourcefor Source Path. To generate an SBOM for the entire repository, leave this field empty. -
Git Branch: The branch of the repository for which you want to generate the SBOM.
-
Workspace: If you cloned the codebase to a different directory than the root workspace directory (
/harness), enter the path to the subdirectory using the format/harness/PATH/TO/SUBDIRECTORY. Leave this field empty if you cloned your codebase into the default directory (/harness). Usually, your codebase is only cloned into a non-default directory if you are cloning multiple codebases into a pipeline. -
SBOM Drift: Select this option if you want to track changes in SBOM. Harness SSCA can detect the changes by comparing the generated SBOM against a specified base/primary SBOM.
Run the pipeline
When the pipeline runs, the SSCA Orchestration step performs the following actions:
- Generates an SBOM in the chosen format for both Containers and Repositories.
- Specifically for Containers:
- Generates and signs an attestation using the provided key and password.
- Stores the SBOM in Harness and uploads the
.attfile to your container registry to accompany the image.
The signed attestation for an Image, stored as an .att file, is placed in the artifact repository alongside the Image.
SBOMs for both Containers and Code Repositories are accessible in the Artifacts view. Additionally, you can locate the SBOM for any artifact on the Supply Chain Assurance tab within the Execution Details page in Harness. For detailed insights, please refer to the view pipeline execution results documentation.
Enforce policies
After generating an SBOM, you can use it to enforce SSCA policies.